Progetto Reti di Computer e Internet
Architettura e Configurazione di Infrastrutture di Rete
Studenti:
Davide Cascella mat:383257
Matteo Migliorati mat:382784
Corso: Laboratorio di Reti
Anno Accademico: 2025-2026
Indice - Parte 1
Introduzione
Requisiti servizi e indirizzamento
Architettura di Rete
Topologia e server di rete
Backbone e Interconnessioni
Collegamenti tra edifici
Configurazione Host
Host degli edifici A, B, C, D, E, DMZ
Configurazione Router
Router Cisco IOS per tutti gli edifici
Server Backup
Configurazione server backup Edificio C
Indice - Parte 2
Server Web
Apache2, permessi e VirtualHost
Server Mail
Sendmail, alias, domini e utenti virtuali
DNS2 Interno Master
Bind9 e zone files per tutti gli edifici
DNS1 Esterno Slave
DNS slave nella DMZ
Server Nagios
Monitoraggio rete
Firewall
iptables interno ed esterno, NAT
Introduzione
Contesto aziendale e sedi
L'azienda Amazin.com è organizzata in 5 edifici con le seguenti caratteristiche:
| Edificio | Num. utenti | Copertura Wi‑Fi |
|---|---|---|
| A | 30 | Sì |
| B | 40 | No |
| C | 40 | No |
| D | 150 | No |
| E | 50 | No |
Requisiti dei servizi
| Servizio | Numero server |
|---|---|
| Posta elettronica | 1 |
| Web | 1 |
| DNS | 2 |
| Backup | 1 |
Indirizzamento e subnetting
| Parametro | Valore |
|---|---|
| Rete privata | 192.168.X.X |
| Subnet mask | 255.255.255.0 (/24) |
| Host per sottorete | 254 utilizzabili |
| Sottoreti assegnate | 6 (una per edificio e dmz) |
Assegnazione sottoreti
| Sede | Sottorete | Capienza |
|---|---|---|
| A | 192.168.3.0/24 | 30 |
| B | 192.168.2.0/24 | 40 |
| C | 192.168.5.0/24 | 40 |
| D | 192.168.1.0/24 | 150 |
| E | 192.168.4.0/24 | 50 |
| B (DMZ) | 192.168.10.0/24 | — |
Architettura di Rete
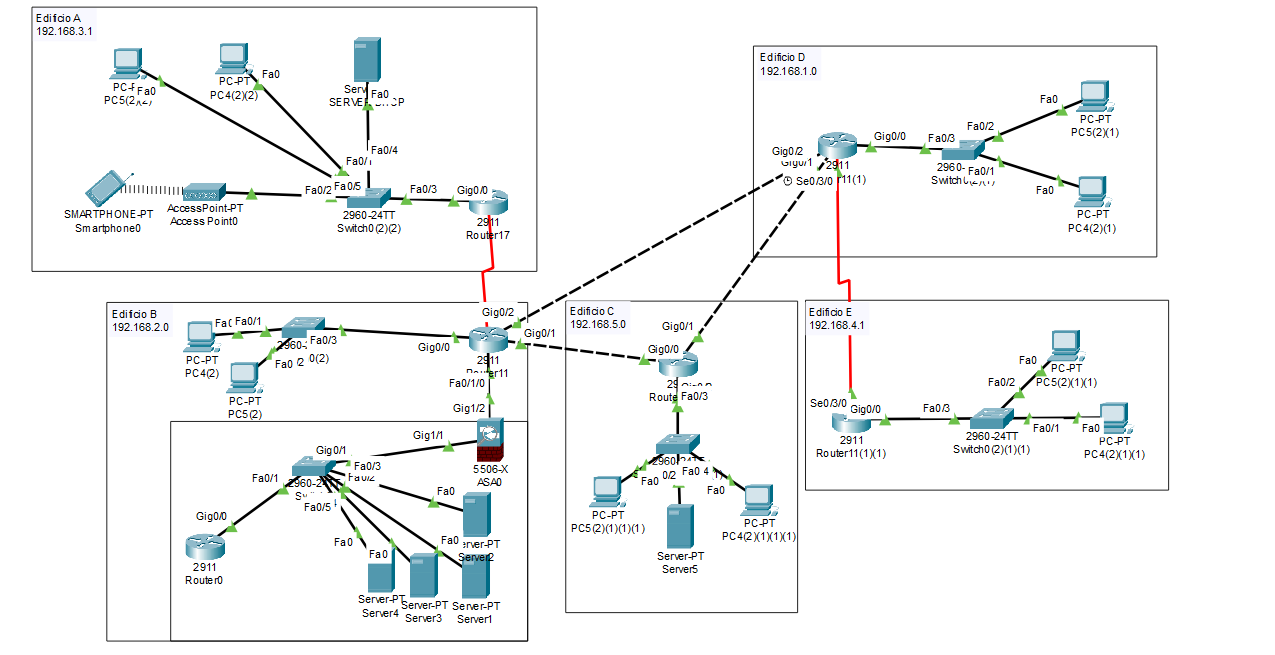
Topologia e routing
La rete adotta una topologia a stella per gli edifici A, B, C e D, con un tratto a bus che collega D ed E. L'accesso alla rete esterna è gestito centralmente dall'edificio B, garantendo una distanza massima di 2 hop verso Internet. Ogni edificio è dotato di un router e i collegamenti inter‑sede sono realizzati in fibra ottica. Come protocollo di routing interno si utilizza RIP, adeguato alle dimensioni contenute dell'infrastruttura.
Sicurezza e connettività
Firewall dedicati gestiscono l'accesso ai servizi pubblici (server web e posta elettronica) ospitati nell'edificio B. L'edificio A dispone di un Access Point Wi‑Fi per garantire copertura wireless agli utenti mobili. Il server di backup è collocato nell'edificio C, scelto per l'elevata interconnessione con gli altri nodi, il carico utenti moderato e l'assenza di Wi‑Fi che riduce la superficie d'attacco.
Server e servizi di rete
| Sede | Servizio | IP server |
|---|---|---|
| B | Posta elettronica | 192.168.10.2 |
| B | Web | 192.168.10.4 |
| B | DNS Esterno slave 1 | 192.168.10.3 |
| B | Nagios | 192.168.10.30 |
| C | DNS Interno Master 2 | 192.168.5.2 |
| C | Backup | 192.168.5.3 |
Backbone e Interconnessioni
Configurazione backbone inter-router
La backbone tra i vari router è costituita utilizzando come indirizzamento IP 10.0.0.0/30, in modo che ogni sottorete punto-punto abbia due indirizzi IP utilizzabili per i collegamenti diretti tra router.
Assegnazione indirizzi backbone
| Collegamento | Router 1 | IP Router 1 | Router 2 | IP Router 2 |
|---|---|---|---|---|
| Backbone 1 | B | 10.0.0.1 | C | 10.0.0.2 |
| Backbone 2 | C | 10.0.0.5 | D | 10.0.0.6 |
| Backbone 3 | B | 10.0.0.9 | D | 10.0.0.10 |
| Backbone 4 | B | 10.0.0.13 | A | 10.0.0.14 |
| Backbone 5 | E | 10.0.0.17 | D | 10.0.0.18 |
| Backbone 6 | B | 10.0.0.21 | BDMZ | 10.0.0.22 |
Configurazione Host
Edificio A
DHCPRete: 192.168.3.0/24
IP host: 192.168.3.10 - 192.168.3.40
DNS1: 192.168.5.2
DNS2: 192.168.10.3
# /etc/network/interfaces
iface enp0s3 inet dhcp
# Riavvia networking
sudo systemctl restart networkingL'edificio A presenta un Server DHCP che si occupa dell'assegnazione automatica degli indirizzi agli host.
Edificio B
StaticoRete: 192.168.2.0/24
IP host: 192.168.2.10 - 192.168.2.50
DNS1: 192.168.5.2
DNS2: 192.168.10.3
# /etc/network/interfaces
iface enp0s3 inet static
address 192.168.2.11
netmask 255.255.255.0
gateway 192.168.2.1
dns-nameservers 192.168.5.2 192.168.10.3
# Riavvia networking
sudo systemctl restart networkingConfigurazione Host
Edificio C
StaticoRete: 192.168.5.0/24
IP host: 192.168.5.10 - 192.168.5.50
DNS1: 192.168.5.2
DNS2: 192.168.10.3
# /etc/network/interfaces
iface enp0s3 inet static
address 192.168.5.11
netmask 255.255.255.0
gateway 192.168.5.1
dns-nameservers 192.168.5.2 192.168.10.3
# Riavvia networking
sudo systemctl restart networkingEdificio D
StaticoRete: 192.168.1.0/24
IP host: 192.168.1.10 - 192.168.1.160
DNS1: 192.168.5.2
DNS2: 192.168.10.3
# /etc/network/interfaces
iface enp0s3 inet static
address 192.168.1.11
netmask 255.255.255.0
gateway 192.168.1.1
dns-nameservers 192.168.5.2 192.168.10.3
# Riavvia networking
sudo systemctl restart networkingConfigurazione Host
Edificio E
StaticoRete: 192.168.4.0/24
IP host: 192.168.4.10 - 192.168.4.60
DNS1: 192.168.5.2
DNS2: 192.168.10.3
# /etc/network/interfaces
iface enp0s3 inet static
address 192.168.4.11
netmask 255.255.255.0
gateway 192.168.4.1
dns-nameservers 192.168.5.2 192.168.10.3
# Riavvia networking
sudo systemctl restart networkingEdificio B (DMZ)
StaticoRete: 192.168.10.0/24
IP host: 192.168.10.100 - 192.168.10.200
DNS1: 192.168.5.2
DNS2: 192.168.10.3
# /etc/network/interfaces
iface enp0s3 inet static
address 192.168.10.101
netmask 255.255.255.0
gateway 192.168.10.1
dns-nameservers 192.168.5.2 192.168.10.3
# Riavvia networking
sudo systemctl restart networkingConfigurazione Router
Router Edificio A
Cisco IOSLAN: 192.168.3.1/24
WAN: 10.0.0.14/30 (verso B)
DNS: 192.168.5.2
enable
configure terminal
interface FastEthernet0/0
ip address 192.168.3.1 255.255.255.0
no shutdown
interface GigabitEthernet0/1
ip address 10.0.0.14 255.255.255.252
no shutdown
router rip
version 2
network 192.168.3.0
network 10.0.0.0
end
ip domain-lookup
ip name-server 192.168.5.2Configurazione Router
Router Edificio B
Cisco IOSLAN: 192.168.2.1/24
WAN: 10.0.0.1/30 (C), 10.0.0.9/30 (D), 10.0.0.13/30 (A), 10.0.0.21/30 (DMZ)
DNS: 192.168.5.2
enable
configure terminal
interface FastEthernet0/0
ip address 192.168.2.1 255.255.255.0
no shutdown
interface GigabitEthernet0/1
ip address 10.0.0.1 255.255.255.252
no shutdown
interface GigabitEthernet1/1
ip address 10.0.0.9 255.255.255.252
no shutdown
interface GigabitEthernet1/2
ip address 10.0.0.13 255.255.255.252
no shutdown
interface GigabitEthernet1/3
ip address 10.0.0.21 255.255.255.252
no shutdown
router rip
version 2
network 192.168.2.0
network 10.0.0.0
end
ip domain-lookup
ip name-server 192.168.5.2Configurazione Router
Router Edificio C
Cisco IOSLAN: 192.168.5.1/24
WAN: 10.0.0.2/30 (verso B), 10.0.0.5/30 (verso D)
DNS: 192.168.5.2
enable
configure terminal
interface FastEthernet0/0
ip address 192.168.5.1 255.255.255.0
no shutdown
interface GigabitEthernet1/1
ip address 10.0.0.2 255.255.255.252
no shutdown
interface GigabitEthernet1/2
ip address 10.0.0.5 255.255.255.252
no shutdown
router rip
version 2
network 192.168.5.0
network 10.0.0.0
end
ip domain-lookup
ip name-server 192.168.5.2Configurazione Router
Router Edificio D
Cisco IOSLAN: 192.168.1.1/24
WAN: 10.0.0.6/30 (C), 10.0.0.10/30 (B), 10.0.0.18/30 (E)
DNS: 192.168.5.2
enable
configure terminal
interface FastEthernet0/0
ip address 192.168.1.1 255.255.255.0
no shutdown
interface GigabitEthernet0/1
ip address 10.0.0.6 255.255.255.252
no shutdown
interface GigabitEthernet1/1
ip address 10.0.0.10 255.255.255.252
no shutdown
interface GigabitEthernet1/2
ip address 10.0.0.18 255.255.255.252
no shutdown
router rip
version 2
network 192.168.1.0
network 10.0.0.0
end
ip domain-lookup
ip name-server 192.168.5.2Configurazione Router
Router Edificio E
Cisco IOSLAN: 192.168.4.1/24
WAN: 10.0.0.17/30 (verso D)
DNS: 192.168.5.2
enable
configure terminal
interface FastEthernet0/0
ip address 192.168.4.1 255.255.255.0
no shutdown
interface GigabitEthernet0/1
ip address 10.0.0.17 255.255.255.252
no shutdown
router rip
version 2
network 192.168.4.0
network 10.0.0.0
end
ip domain-lookup
ip name-server 192.168.5.2Configurazione Router
Router Edificio B (DMZ)
Cisco IOSLAN: 192.168.10.1/24
WAN: 10.0.0.22/30 (verso B)
DNS: 192.168.5.2
enable
configure terminal
interface FastEthernet0/0
ip address 192.168.10.1 255.255.255.0
no shutdown
interface GigabitEthernet0/1
ip address 10.0.0.22 255.255.255.252
no shutdown
router rip
version 2
network 192.168.10.0
network 10.0.0.0
end
ip domain-lookup
ip name-server 192.168.5.2Configurazione Servizi
Server Backup - Edificio C
IP: 192.168.5.3Rete: 192.168.5.0/24
IP Server: 192.168.5.3
Gateway: 192.168.5.1
Broadcast: 192.168.5.255
Configurazione su macchina reale:
~# sudo nano /etc/network/interfaces
#iface enp0s3 inet dhcp
iface enp0s3 inet static
address 192.168.5.3
netmask 255.255.255.0
network 192.168.5.0
broadcast 192.168.5.255
gateway 192.168.5.1
~# sudo systemctl restart networkingConfigurazione Servizi
Server Web - Edificio B (DMZ)
IP: 192.168.10.4Rete: 192.168.10.0/24
IP Server: 192.168.10.4
Gateway: 192.168.10.1
Dominio: www.amazin.com
~# sudo nano /etc/network/interfaces
iface enp0s3 inet static
address 192.168.10.4
netmask 255.255.255.0
network 192.168.10.0
broadcast 192.168.10.255
gateway 192.168.10.1Innanzitutto aggiungiamo l'ip e dominio a /etc/hosts inserendo questa riga
127.0.0.1 www.amazin.comPoi installiamo apache2, configurandolo per gestire le richieste, la configurazione si trova in etc/apache2/apache2.conf
Nel file /etc/apache2/sites-available/000-default.conf aggiungiamo le righe:
ServerName www.amazin.com
UseCanonicalName OffConfigurazione Servizi
Server Web - Permessi e Log
Apache2 ConfigurationCi creiamo una cartella per ospitare il sito in: /var/www/amazin.com/it
Per la sicurezza del server possiamo gestire i permessi in questo modo:
Nella cartella "/var/www/amazin.com/it/" impostiamo i permessi in questo modo:
L'owner delle cartelle nella directory a 7 (tutti i permessi), il gruppo e tutti gli altri a 5 (lettura ed esecuzione) 755
Mentre per tutti i file l'accesso dell'admin è 6 (scrittura e lettura), per il gruppo e gli altri 4 (sola lettura) 644
In fine impostiamo l'admin come proprietario della cartella /var/www/amazin.com
Sempre ai fini della sicurezza del sito possiamo configurare i log di apache2. Creiamo una cartella per i log in /var/log/apache2/amazin.com
Cambiamo il proprietario della cartella /var/log/apache2/amazin.com
Configurazione Servizi
Server Web - VirtualHost
Apache2 VirtualHostCreiamo un file che crea i log amazin.com.conf. Intera configurazione del file:
ServerAdmin davide@amazin.com
ServerName amazin.com
ServerAlias www.amazin.com
DocumentRoot /var/www/amazin.com
ErrorLog ${APACHE_LOG_DIR}/amazin.com/error.log
CustomLog ${APACHE_LOG_DIR}/amazin.com/access.log combined
Options Indexes FollowSymLinks
AllowOverride All
Require all granted
sudo a2ensite amazin.com.conf
sudo systemctl reload apache2
sudo systemctl restart apache2Configurazione Servizi
Server Mail - Edificio B (DMZ)
IP: 192.168.10.2~# nano /etc/network/interfaces
#iface enp0s3 inet dhcp
iface enp0s3 inet static
address 192.168.10.2
netmask 255.255.255.0
network 192.168.10.0
broadcast 192.168.10.255
gateway 192.168.10.1Ora impostiamo i permessi ed i controlli per i client che si connettono al server di posta in /etc/mail/access
Connect:192.168
GreetPause:192.168
ClientRate:192.168
ClientConn:192.168
FREE.STREALTH.MAILER@ 550
amazin.com RELAY
192.168 RELAYConfigurazione Servizi
Server Mail - Alias
SendmailAlias nel file /etc/mail/aliases
postmaster: davide
admin: davide,matteo
dmz: admindmz
retea: adminretea
reteb: adminreteb
retec: adminretec
reted: adminreted
retee: adminretee
admindmz: matteo
adminretea: orro, antropova
adminreteb: matteo, giannelli
adminretec: davide, sylla
adminreted: matteo, salvadori
adminretee: dag, davideConfigurazione Servizi
Server Mail - Domini e Relay
SendmailConfiguriamo nomi di dominio gestiti dal server /etc/mail/local-host-names
localhost
amazin.com
mail.amazin.com
dmz.amazin.com
retea.amazin.com
reteb.amazin.com
retec.amazin.com
reted.amazin.com
retee.amazin.comConfiguriamo /etc/mail/sendmail.mc
FEATURE(`relay_entire_domain')dnlConfigurazione Servizi
Server Mail - Utenti Virtuali
SendmailCreazione di utenti di sistema
useradd --create-home -s /sbin/nologin davide; passwd admin32
useradd --create-home -s /sbin/nologin matteo; passwd admin12Configuriamo la tabella degli utenti virtuali /etc/mail/virtusertable
root@amazin.com root
postmaster@amazin.com postmaster
admin@amazin.com admin
dmz@amazin.com dmz
retea@amazin.com retea
reteb@amazin.com reteb
retec@amazin.com retec
reted@amazin.com reted
retee@amazin.com retee
davide@amazin.com davide
matteo@amazin.com matteocd /etc/mail
make
service sendmail restartConfigurazione Servizi
DNS2 Interno Master - Edificio C
IP: 192.168.5.2~# sudo nano /etc/network/interfaces
iface enp0s3 inet static
address 192.168.5.2
netmask 255.255.255.0
network 192.168.5.0
broadcast 192.168.5.255
gateway 192.168.5.1
~# sudo systemctl restart networkingresolv.conf
domain amazin.com
nameserver 192.168.5.2
nameserver 192.168.10.3Configurazione Servizi
DNS2 Interno - named.conf
Bind9 Configurationnamed.conf - ACL e Options
acl localhost {
127.0.0.1;
};
acl dmz {
192.168.10.0/24;
};
acl trusted-networks {
192.168.1.0/24;
192.168.2.0/24;
192.168.3.0/24;
192.168.4.0/24;
192.168.5.0/24;
};
options {
directory "/var/cache/bind";
dnssec-validation auto;
auth-nxdomain no;
version "Not disclosed";
notify yes;
allow-transfer { none; };
allow-query { localhost; trusted-networks; };
forwarders {
1.1.1.1;
};
recursion yes;
max-cache-size 512M;
query-timeout 10;
};Configurazione Servizi
DNS2 Interno - Zone Configuration
Bind9 Zonesnamed.conf - Zone Master
// DMZ
zone "dmz.amazin.com" {
type master;
file "/etc/bind/zones/dmz.amazin.com.db";
};
zone "10.168.192.in-addr.arpa" {
type master;
file "/etc/bind/zones/10.168.192.in-addr.arpa.db";
};
// Edificio A
zone "edificioa.amazin.com" {
type master;
file "/etc/bind/zones/edificioa.amazin.com.db";
};
zone "3.168.192.in-addr.arpa" {
type master;
file "/etc/bind/zones/3.168.192.in-addr.arpa.db";
};
// Edificio B
zone "edificiob.amazin.com" {
type master;
file "/etc/bind/zones/edificiob.amazin.com.db";
};
zone "2.168.192.in-addr.arpa" {
type master;
file "/etc/bind/zones/2.168.192.in-addr.arpa.db";
};Configurazione Servizi
DNS2 Interno - Zone Configuration
Bind9 Zones// Edificio C
zone "edificioc.amazin.com" {
type master;
file "/etc/bind/zones/edificioc.amazin.com.db";
};
zone "5.168.192.in-addr.arpa" {
type master;
file "/etc/bind/zones/5.168.192.in-addr.arpa.db";
allow-transfer { none };
};
// Edificio D
zone "edificiod.amazin.com" {
type master;
file "/etc/bind/zones/edificiod.amazin.com.db";
};
zone "1.168.192.in-addr.arpa" {
type master;
file "/etc/bind/zones/1.168.192.in-addr.arpa.db";
};
// Edificio E
zone "edificioe.amazin.com" {
type master;
file "/etc/bind/zones/edificioe.amazin.com.db";
};
zone "4.168.192.in-addr.arpa" {
type master;
file "/etc/bind/zones/4.168.192.in-addr.arpa.db";
};Configurazione Servizi
DNS2 - Zone File DMZ
dmz.amazin.com.db/etc/bind/zones/dmz.amazin.com.db
$TTL 86400
@ IN SOA dns1.dmz.amazin.com. admin.amazin.com. (
2025102001 ; Serial
3600 ; Refresh
1800 ; Retry
1209600 ; Expire
86400 ; Minimum TTL
)
@ IN NS dns1.dmz.amazin.com.
@ IN NS dmz.amazin.com.
@ IN MX 10 mail.amazin.com.
dns1 IN A 192.168.10.3
nagios IN A 192.168.10.30
web IN A 192.168.10.4
mail IN A 192.168.10.2Configurazione Servizi
DNS2 - Zone File DMZ Reverse
10.168.192.in-addr.arpa.db/etc/bind/zones/10.168.192.in-addr.arpa.db
$TTL 86400
@ IN SOA dns1.dmz.amazin.com. admin.amazin.com. (
2025102001 ; Serial
3600 ; Refresh
1800 ; Retry
1209600 ; Expire
86400 ; Minimum TTL
)
@ IN NS dns1.dmz.amazin.com.
@ IN NS dmz.amazin.com.
30 IN PTR nagios.dmz.amazin.com.
4 IN PTR web.dmz.amazin.com.
3 IN PTR dns1.dmz.amazin.com.
2 IN PTR mail.dmz.amazin.com.Configurazione Servizi
DNS2 - Zone File Edificio A
edificioa.amazin.com.db/etc/bind/zones/edificioa.amazin.com.db
$TTL 86400
@ IN SOA dns1.dmz.amazin.com. admin.amazin.com. (
2025102001 ; Serial
3600 ; Refresh
1800 ; Retry
1209600 ; Expire
86400 ; Minimum TTL
)
IN NS dns1.dmz.amazin.com.
gw IN A 192.168.3.1
h.3.10 IN A 192.168.3.10
h.3.11 IN A 192.168.3.11/etc/bind/zones/3.168.192.in-addr.arpa.db
$TTL 86400
@ IN SOA dns1.dmz.amazin.com. admin.amazin.com. (
2025102001 ; Serial
3600 ; Refresh
1800 ; Retry
1209600 ; Expire
86400 ; Minimum TTL
)
IN NS dns1.dmz.amazin.com.
1 IN PTR gateway
10 IN PTR h.3.10
11 IN PTR h.3.11Configurazione Servizi
DNS2 - Zone File Edificio B
edificiob.amazin.com.db/etc/bind/zones/edificiob.amazin.com.db
$TTL 86400
@ IN SOA dns1.dmz.amazin.com. admin.amazin.com. (
2025060202 ; Serial
3600 ; Refresh
1800 ; Retry
1209600 ; Expire
86400 ; Minimum TTL
)
IN NS dns1.dmz.amazin.com.
gw IN A 192.168.2.1
H.2.10 IN A 192.168.2.10
H.2.11 IN A 192.168.2.11/etc/bind/zones/2.168.192.in-addr.arpa.db
$TTL 86400
@ IN SOA dns1.dmz.amazin.com. admin.amazin.com. (
2025060202 ; Serial
3600 ; Refresh
1800 ; Retry
1209600 ; Expire
86400 ; Minimum TTL
)
IN NS dns1.dmz.amazin.com.
1 IN PTR gateway
10 IN PTR H.2.10
11 IN PTR H.2.11Configurazione Servizi
DNS2 - Zone File Edificio C
edificioc.amazin.com.db/etc/bind/zones/edificioc.amazin.com.db
$TTL 86400
@ IN SOA dns1.dmz.amazin.com. admin.amazin.com. (
2025060202 ; Serial
3600 ; Refresh
1800 ; Retry
1209600 ; Expire
86400 ; Minimum TTL
)
IN NS dns1.dmz.amazin.com.
gw IN A 192.168.5.1
H.5.10 IN A 192.168.5.10
H.5.11 IN A 192.168.5.11/etc/bind/zones/5.168.192.in-addr.arpa.db
$TTL 86400
@ IN SOA dns1.dmz.amazin.com. admin.amazin.com. (
2025060202 ; Serial
3600 ; Refresh
1800 ; Retry
1209600 ; Expire
86400 ; Minimum TTL
)
IN NS dns1.dmz.amazin.com.
1 IN PTR gateway
10 IN PTR H.5.10
11 IN PTR H.5.11Configurazione Servizi
DNS2 - Zone File Edificio D
edificiod.amazin.com.db/etc/bind/zones/edificiod.amazin.com.db
$TTL 86400
@ IN SOA dns1.dmz.amazin.com. admin.amazin.com. (
2025060202 ; Serial
3600 ; Refresh
1800 ; Retry
1209600 ; Expire
86400 ; Minimum TTL
)
IN NS dns1.dmz.amazin.com.
gw IN A 192.168.1.1
H.1.10 IN A 192.168.1.10
H.1.11 IN A 192.168.1.11/etc/bind/zones/1.168.192.in-addr.arpa.db
$TTL 86400
@ IN SOA dns1.dmz.amazin.com. admin.amazin.com. (
2025060202 ; Serial
3600 ; Refresh
1800 ; Retry
1209600 ; Expire
86400 ; Minimum TTL
)
IN NS dns1.dmz.amazin.com.
1 IN PTR gateway
10 IN PTR H.1.10
11 IN PTR H.1.11Configurazione Servizi
DNS2 - Zone File Edificio E
edificioe.amazin.com.db/etc/bind/zones/edificioe.amazin.com.db
$TTL 86400
@ IN SOA dns1.dmz.amazin.com. admin.amazin.com. (
2025060202 ; Serial
3600 ; Refresh
1800 ; Retry
1209600 ; Expire
86400 ; Minimum TTL
)
IN NS dns1.dmz.amazin.com.
gw IN A 192.168.4.1
H.4.10 IN A 192.168.4.10
H.4.11 IN A 192.168.4.11/etc/bind/zones/4.168.192.in-addr.arpa.db
$TTL 86400
@ IN SOA dns1.dmz.amazin.com. admin.amazin.com. (
2025060202 ; Serial
3600 ; Refresh
1800 ; Retry
1209600 ; Expire
86400 ; Minimum TTL
)
IN NS dns1.dmz.amazin.com.
1 IN PTR gateway
10 IN PTR H.4.10
11 IN PTR H.4.11Configurazione Servizi
DNS1 Esterno Slave - Edificio B (DMZ)
IP: 192.168.10.3~# sudo nano /etc/network/interfaces
iface enp0s3 inet static
address 192.168.10.3
netmask 255.255.255.0
network 192.168.10.0
broadcast 192.168.10.255
gateway 192.168.10.1
~# sudo systemctl restart networkingresolv.conf
domain amazin.com
nameserver 192.168.5.2Configurazione Servizi
DNS1 Esterno - named.conf
Bind9 Configurationnamed.conf
options {
directory "/var/cache/bind";
dnssec-validation auto;
auth-nxdomain no;
version "Not disclosed";
notify yes;
allow-transfer { none; };
allow-query { any; };
recursion no;
};
// DNS1 è slave di DNS2
zone "dmz.amazin.com" {
type slave;
file "/etc/bind/zones/dmz.amazin.com.bk";
masters { 192.168.5.2; };
};
// reverse mapping per amazin.com
zone "10.168.192.in-addr.arpa" {
type slave;
file "/etc/bind/zones/5.168.192.in-addr.arpa.bk";
masters { 192.168.5.2; };
};Configurazione Servizi
Server Nagios - Edificio B (DMZ)
IP: 192.168.10.30Rete: 192.168.10.0/24
IP Server: 192.168.10.30
Gateway: 192.168.10.1
Servizio: Monitoraggio Rete
~# sudo nano /etc/network/interfaces
iface enp0s3 inet static
address 192.168.10.30
netmask 255.255.255.0
network 192.168.10.0
broadcast 192.168.10.255
gateway 192.168.10.1
dns-nameservers 192.168.5.2 192.168.10.3
~# sudo systemctl restart networkingConfigurazione Firewall
Firewall Interno (IN)
iptablesAbbiamo due firewall: uno interno, che implementa più misure di protezione essendo appunto interno alla nostra rete; e uno esterno, il quale avrà meno misure di protezione dovendo essere accessibile dall'esterno.
Inizializzazione e policy di default
iptables -F FORWARD
iptables -F INPUT
iptables -F OUTPUT
iptables -P FORWARD DROP
iptables -P INPUT DROP
iptables -P OUTPUT DROPRegole per DNS2
iptables -A FORWARD -p udp -d 192.168.5.2 --dport 53 -j ACCEPT
iptables -A FORWARD -p tcp -d 192.168.5.2 --dport 53 -j ACCEPTConfigurazione Firewall
Firewall Interno (IN) - Regole Applicative
iptablesRegole per posta elettronica
iptables -A FORWARD -p tcp -d 192.168.10.2 --dport 25 -m limit --limit 100/s -j ACCEPT
iptables -A FORWARD -p tcp -d 192.168.10.2 --dport 110 -m limit --limit 100/s -j ACCEPT
iptables -A FORWARD -p tcp -d 192.168.10.2 --dport 143 -m limit --limit 100/s -j ACCEPTRegole per web
iptables -A FORWARD -p tcp -d 192.168.10.4 --dport 443 -m limit --limit 100/s -j ACCEPTRegole per connessioni già stabilite
iptables -A OUTPUT -m state --state ESTABLISHED,RELATED -j ACCEPT
iptables -A INPUT -m state --state ESTABLISHED,RELATED -j ACCEPT
iptables -A FORWARD -m state --state ESTABLISHED,RELATED -j ACCEPTConfigurazione Firewall
Firewall Esterno (OUT)
iptablesRegole per DNS1, posta elettronica e web
iptables -A FORWARD -p tcp -d 192.168.10.2 --dport 25 -j ACCEPT
iptables -A FORWARD -p tcp -d 192.168.10.2 --dport 110 -j ACCEPT
iptables -A FORWARD -p tcp -d 192.168.10.2 --dport 143 -j ACCEPT
iptables -A FORWARD -p tcp -d 192.168.10.3 --dport 53 -j ACCEPT
iptables -A FORWARD -p udp -d 192.168.10.3 --dport 53 -j ACCEPT
iptables -A FORWARD -p tcp -d 192.168.10.4 --dport 443 -j ACCEPTRegole per connessioni già stabilite
iptables -A FORWARD -m state --state ESTABLISHED,RELATED -j ACCEPT
iptables -A FORWARD -p tcp -j REJECT --reject-with tcp-resetConfigurazione Firewall
Firewall Esterno (OUT) - NAT
iptables NATRegole per NAT
iptables -t nat -A PREROUTING -p tcp --dport 25 -j DNAT --to-destination 192.168.10.2
iptables -t nat -A PREROUTING -p udp --dport 53 -j DNAT --to-destination 192.168.10.3
iptables -t nat -A PREROUTING -p tcp --dport 53 -j DNAT --to-destination 192.168.10.3
iptables -t nat -A PREROUTING -p tcp --dport 443 -j DNAT --to-destination 192.168.10.4
iptables -t nat -A POSTROUTING -o eth1 -j MASQUERADE